In an era where software development is increasingly reliant on open-source packages, the discovery of malicious entities within these resources poses a significant challenge to the security and integrity of software projects. Recent findings by Checkmarx have shed light on a particularly insidious threat lurking within the Python Package Index (PyPI): a series of seemingly benign packages that, in reality, harbor the malicious BlazeStealer malware. This revelation underscores the imperative for developers to adopt stringent security measures in their engagement with open-source libraries.
Unveiling the Threat: Technical Insights into BlazeStealer
The investigation, initiated in January 2023, unveiled eight packages – Pyobftoexe, Pyobfusfile, Pyobfexecute, Pyobfpremium, Pyobflite, Pyobfadvance, Pyobfuse, and Pyobfgood – as carriers of the BlazeStealer malware. This dangerous code is designed to execute a range of malicious activities, from harvesting sensitive information, such as passwords and screenshots, to executing arbitrary commands, encrypting files, and even disabling Microsoft Defender Antivirus. The malware leverages a Discord bot for seamless communication between the compromised system and the attacker, indicating a sophisticated approach to cyber-attacks. The majority of downloads for these tainted packages have been traced back to the U.S., China, and Russia, with notable activities extending to several other countries.
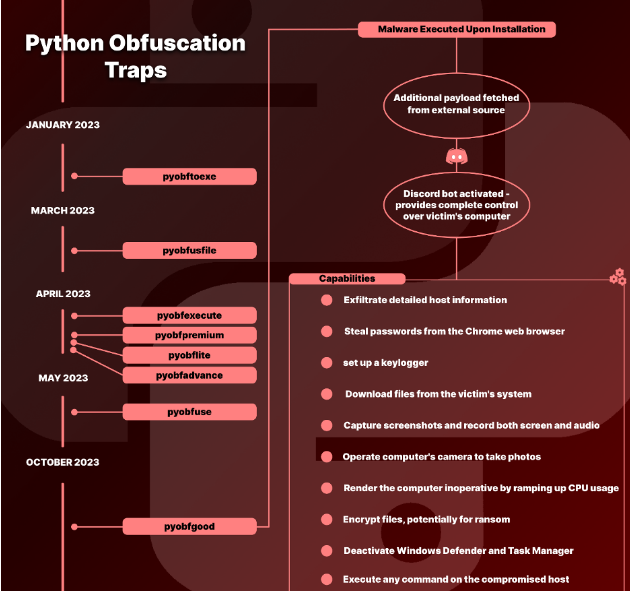
Source: Checkmarx
Furthermore, Checkmarx’s findings are part of a broader trend, with similar threats detected in npm modules, highlighting the pervasive nature of this cybersecurity challenge. These discoveries emphasize the critical need for heightened vigilance among developers and security professionals alike.
Strategies for Mitigation: Bolstering Defenses Against Malware
To counteract the threats posed by malicious packages such as those containing BlazeStealer, developers and organizations are advised to adhere to the following practices:
- Thorough Package Assessment: Before incorporating open-source packages into projects, it is crucial to conduct an exhaustive evaluation. This includes scrutinizing community reviews, assessing the activity around the package, and verifying the credibility of the maintainers.
- Regular Security Audits: Implementing routine security audits can proactively identify and mitigate vulnerabilities in software dependencies, ensuring resilience against emerging threats.
- Staying Informed: Maintaining awareness of the latest cybersecurity threats and engaging with security communities can significantly enhance an organization’s defense mechanisms.
- Automated Code Scanning: Incorporating automated code scanning into the development workflow can facilitate early detection and resolution of security issues.
- Community Collaboration: Promoting a culture of information sharing and collaboration within the development community can augment collective security efforts.
- Dependency Versioning: Adopting a disciplined approach to dependency management, including regular updates, can help mitigate security risks.
- Educational Initiatives: Encouraging ongoing education and awareness about secure coding practices among development teams is vital for fostering a security-conscious culture.
Final Thoughts: Navigating the Future of Secure Software Development
The identification of BlazeStealer malware within Python packages on PyPI serves as a stark reminder of the challenges inherent in utilizing open-source software. As the software development landscape continues to evolve, so too do the threats that seek to undermine the security and integrity of projects. By embracing a proactive and informed approach to open-source package selection and management, developers can significantly reduce the risk of inadvertently introducing malware into their projects. Ultimately, the collective efforts of the development community, grounded in diligence, education, and collaboration, will be pivotal in sustaining a secure and resilient open-source ecosystem.
Also Read:
- Enhancing Node.js Application Security: Essential Best Practices
- Maximizing Node.js Efficiency with Clustering and Load Balancing
- Understanding Event Emitters in Node.js for Effective Event Handling
- Understanding Streams in Node.js for Efficient Data Handling
- Harnessing Environment Variables in Node.js for Secure Configurations

