In a recent cybersecurity alert, the notorious Lazarus Group, recognized as a state-sponsored hacking entity from North Korea, has executed a sophisticated scheme to compromise software developers’ systems through the Python Package Index (PyPI). By exploiting typographical errors during package installation, the group successfully uploaded four malicious packages to the repository. This tactic not only demonstrates the evolving sophistication of cyber threats but also underscores the critical need for heightened security awareness among developers.
The Infiltration Strategy
The Lazarus Group’s operation involved the deployment of four packages – pycryptoenv, pycryptoconf, quasarlib, and swapmempool – into the PyPI repository. These packages, now removed, cumulatively amassed 3,269 downloads, indicating the scale of potential compromise. The most downloaded among them, pycryptoconf, accounted for 1,351 downloads. The attackers’ primary aim appears to be the exploitation of typographical errors, a strategy known as “typosquatting”, where developers accidentally download malicious packages instead of the intended ones.
JPCERT/CC, alongside Phylum’s prior discovery of unauthorized npm packages, revealed that this method of attack was not isolated. Both incidents involved the concealment of malicious code within innocuous files, such as a “test.py” script, which in reality harbored an XOR-encoded Dynamic Link Library (DLL) file. This file, upon decryption, facilitated the deployment of additional malware, signaling a concerning trend in software development security breaches.
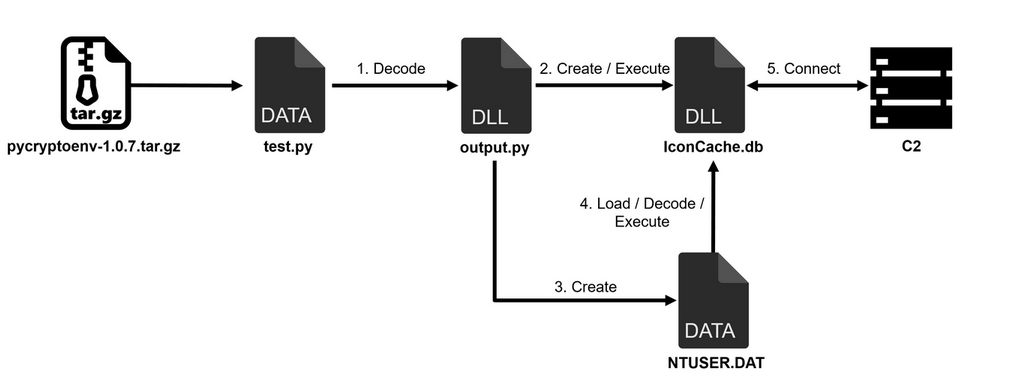
Flow Execution for PyPI Malware (JPCERT)
Understanding the Malware’s Operation
The technical analysis provided by JPCERT/CC sheds light on the malware’s operation. Specifically, it describes how the NTUSER.DAT file is used to execute another malware, Comebacker, which subsequently establishes connections with a command-and-control (C2) server. This server then directs the infected system to fetch and execute a Windows executable file, completing the infection chain. Such tactics highlight the sophistication of the Lazarus Group’s methods and the critical importance of maintaining vigilant security practices.
Recommendations for Safeguarding Your Systems
To combat these and similar threats, several proactive measures are recommended:
- Verification of Packages: Before installing packages from official repositories, verify their authenticity. Checking package signatures and hashes can ensure their integrity.
- Regular Audits: Perform audits regularly within your development environment to identify and eliminate potential vulnerabilities posed by outdated or unnecessary packages.
- Dependency Scanning: Use automated tools for scanning project dependencies to detect known vulnerabilities or suspicious patterns.
- User Education: It’s essential to educate developers on the risks of typosquatting and the importance of meticulous package selection.
- Security Best Practices: Adopt best practices such as using virtual environments and containerization to minimize the impact of security breaches.
- Monitoring and Logging: Implement robust mechanisms for monitoring and logging activities to facilitate the timely detection of and response to security incidents.
- Multi-Factor Authentication (MFA): Adding MFA for accessing critical systems can provide an additional security layer against unauthorized access.
Final Thoughts
The discovery of malicious Python packages on PyPI by the Lazarus Group, exploiting developers’ typographical errors, serves as a stark reminder of the persistent and evolving nature of cyber threats. This incident underscores the importance of diligence, caution, and the adoption of robust security measures in software development environments. By staying informed, regularly updating security practices, and fostering a culture of security awareness, developers can significantly reduce the risk of inadvertently introducing malicious software into their systems, thereby safeguarding their projects and the broader software ecosystem from these insidious threats.
Also Read:
- Enhancing Node.js Application Security: Essential Best Practices
- Maximizing Node.js Efficiency with Clustering and Load Balancing
- Understanding Event Emitters in Node.js for Effective Event Handling
- Understanding Streams in Node.js for Efficient Data Handling
- Harnessing Environment Variables in Node.js for Secure Configurations

